CTF Writeup by Frigyes
Intro
Name: Feb. 2 – Chocolates
Category: Web
Description: The first thing I want to give everyone is chocolate, of course. I found this wonderful company that sells the most exquisite chocolates, but I heard that they sell a super special secret valentine chocolate that’s hidden somewhere on their website. Here’s the website, do you think you can find it for me?
https://chocolates-mhsctf.0xmmalik.repl.co
First, lets open the site and see what we have:
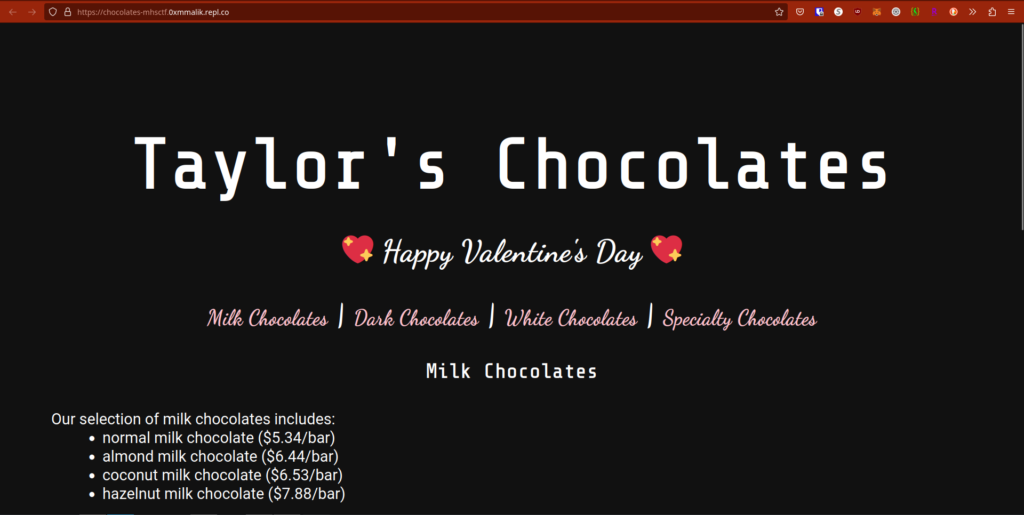
Hmmm… Nothing on the UI. The links in purple just take you to different sections on the website:
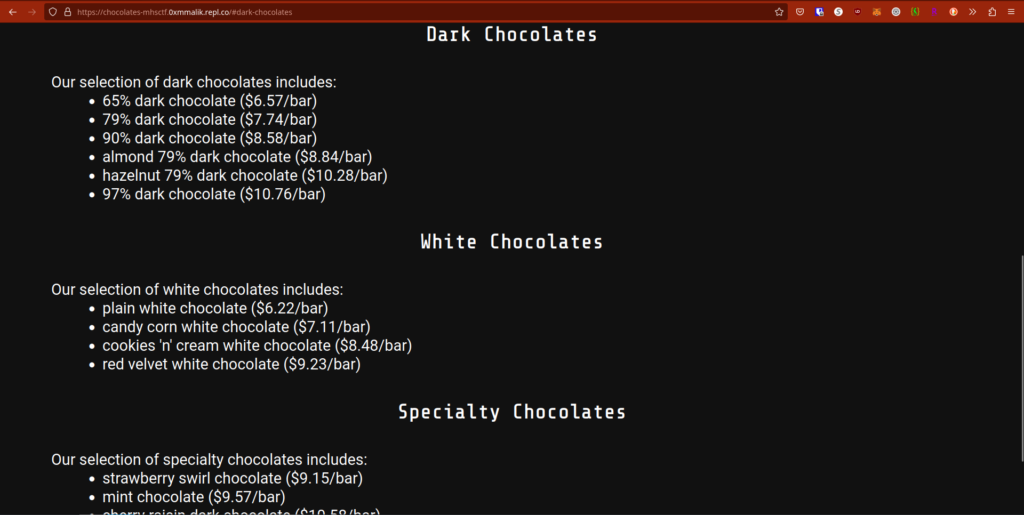
Time to dig deeper!
First, I decided to open page source, maybe we find some juicy details hidden in the HTML file.
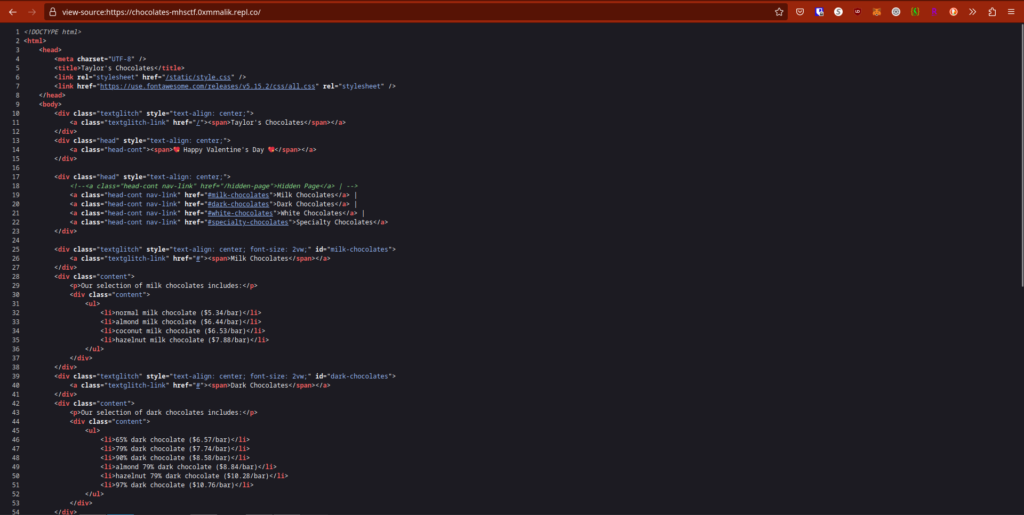
Hidden page? I wonder what that does!

I need a key? I need a key! But where do I get myself a key? Let’s keep digging in the source files for the website. I opened up the inspect tool to start looking around. When I opened the style page: BAM! It was staring at me!

So my key is: ?key=thedarkestchocolate
Let’s try it!
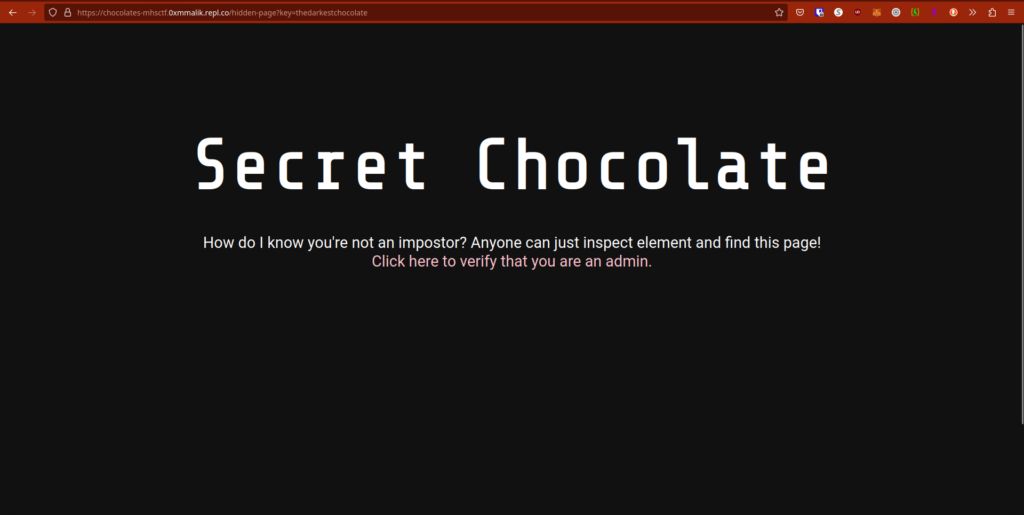
Admin? Me? Of course! *click*

IMPOSTOR?!??!? SUS?
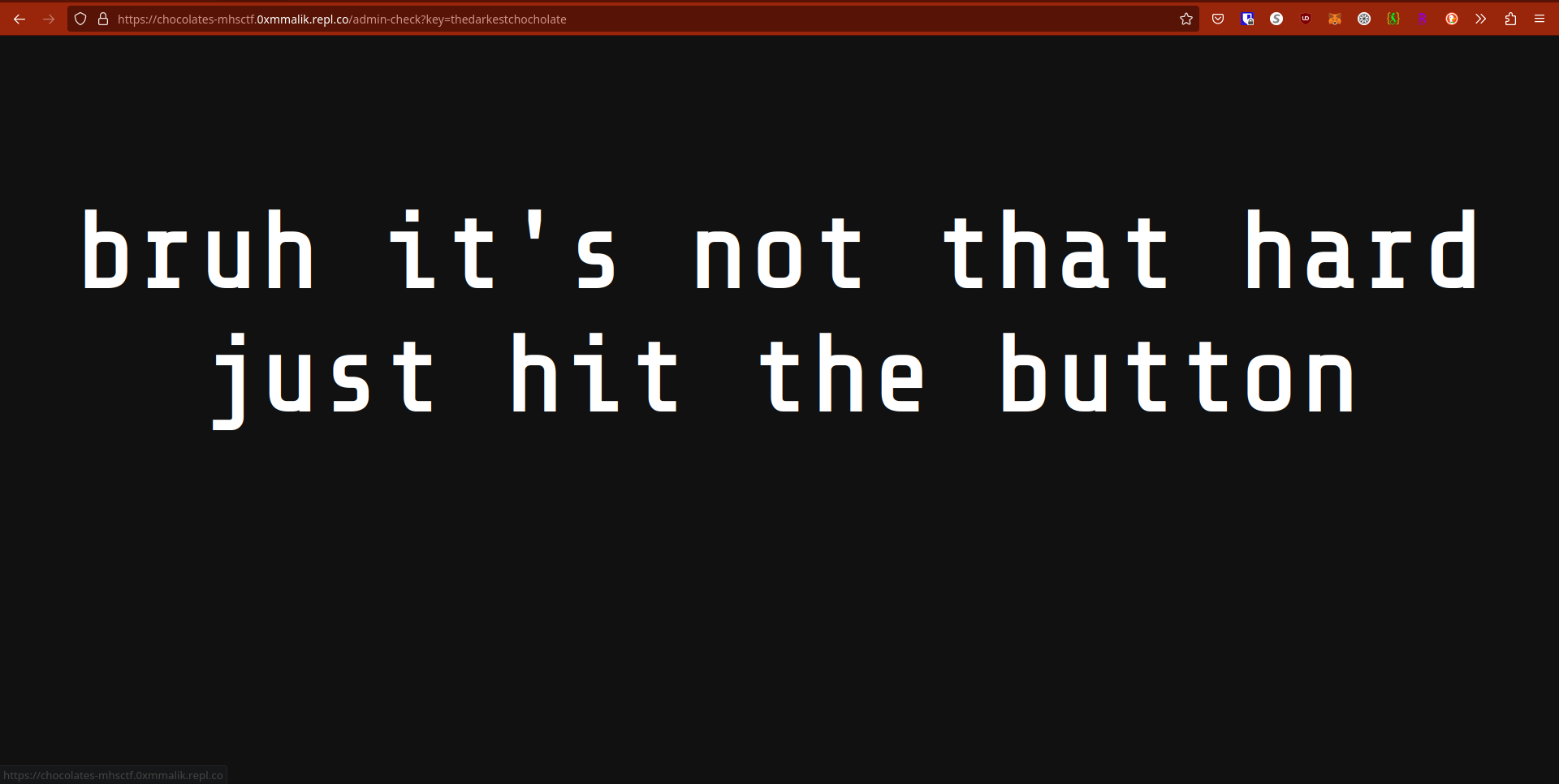
Okay, let’s see what’s going on in here… Changing the key in the URL yields the same page for everything except “anotherkeylol”:
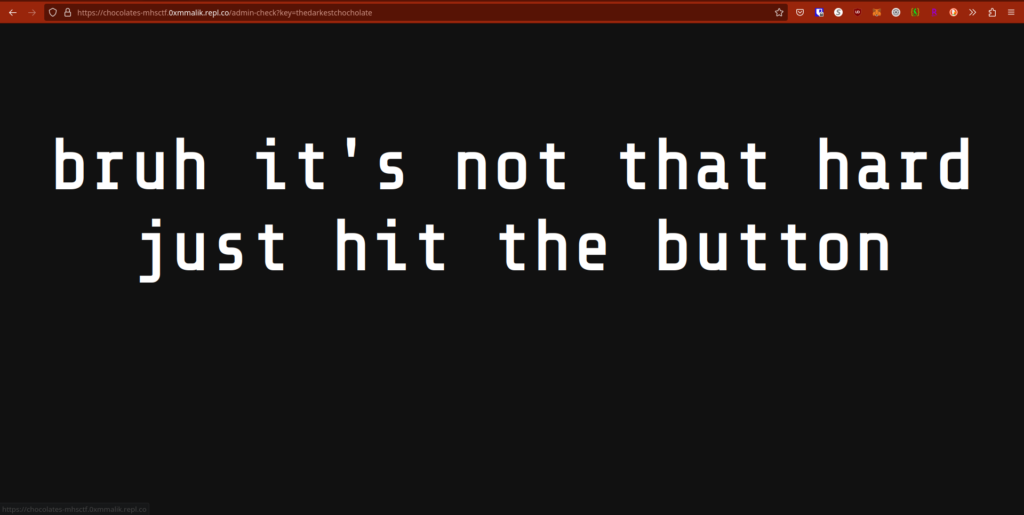
What button? Anyways. Because the only different page (The impostor!!! (amogus (sus))) loaded for key=anotherkeylol, I’m assuming that’s the correct key. Also the CTF admins said don’t brute force the URLs after giving us rockyou.txt… But let’s keep digging!
Cookies for the cookie monster
Back to the inspect tool. I notice two things: First, the page sends code 400 instead of 200. Curious…

Second, we have a session cookie:

When we decode it, it’s a JWT, but it has something that looks like gibberish at the end of it…
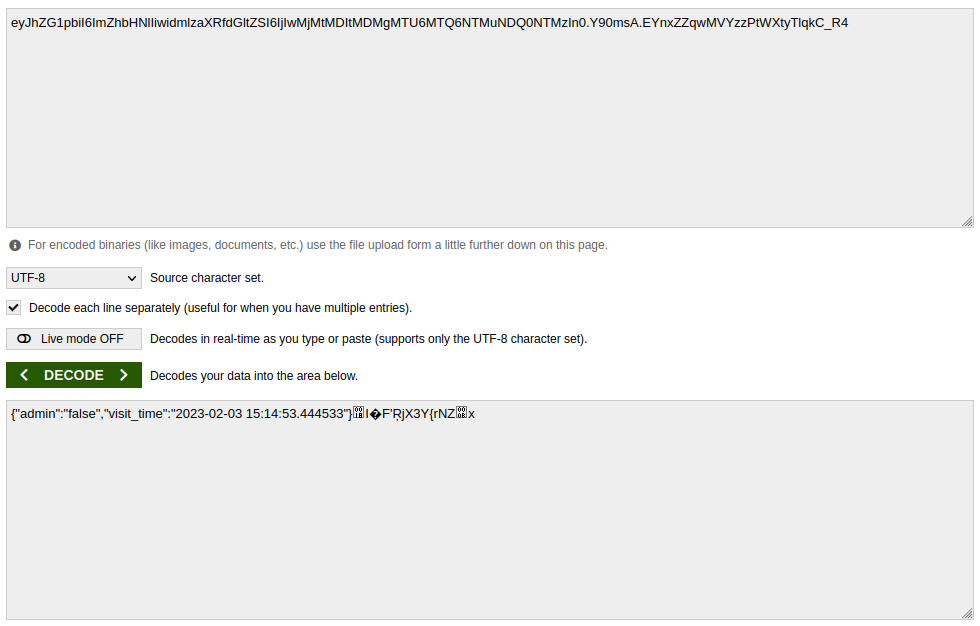
“admin” : “false” hmmmm, what about “admin” : “true”?

Ha! Not that easy! After a bit of googling, I learned about Flask session cookies and flask-unsign. I went ahead and installed flask-unsign, and downloaded rockyou.txt as provided by the organizers. Next, I tried running the cookie trough flask-unsign:
[frigyes@archlaptop ~]$ flask-unsign --unsign --cookie eyJhZG1pbiI6ImZhbHNlIn0.Y90p2g.cmhYNYHl-Oj5C-oH90HIsf3wCbM --no-literal-eval --wordlist ./Desktop/my_site/ctf/rockyou.txt
[*] Session decodes to: {'admin': 'false'}
[*] Starting brute-forcer with 8 threads..
[+] Found secret key after 11648 attempts
b'BATMAN'Yay! A secret key! Now I just need to encode the new cookie with the “secret” key:
[frigyes@archlaptop ~]$ flask-unsign --sign --cookie "{'admin': 'true'}" --secret 'BATMAN'
eyJhZG1pbiI6InRydWUifQ.Y90qig.fqQzzWzIdwF3Ih1AJKV__E_ezqAI paste it into my session cookie, and sure enough:
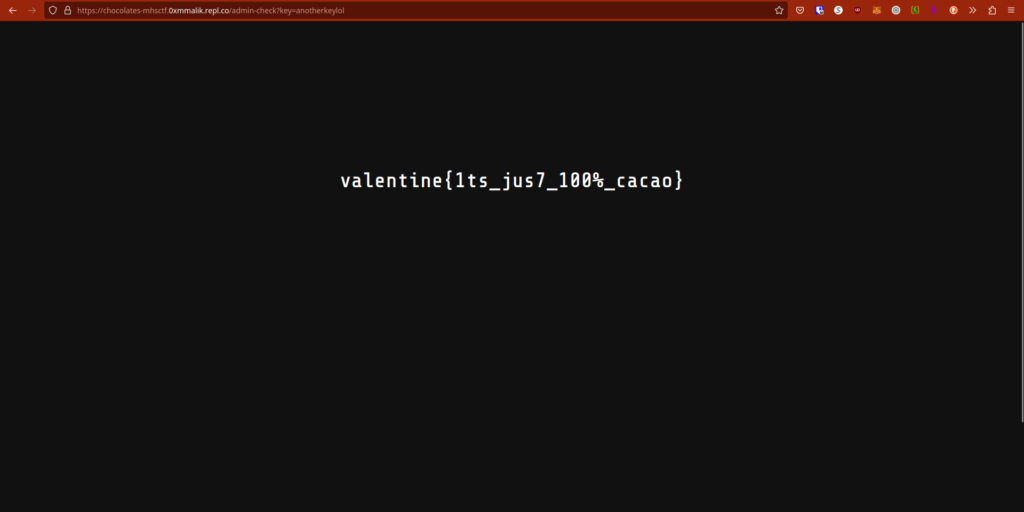
Flag: valentine{1ts_jus7_100%_cacao}
If you liked this writeup, you might also like: The Numbers – PicoCTF writeup