CTF Writeup by Frigyes
Introduction
This challenge was originally featured on LA CTF 2023
Category: misc
Description: I was trying to send a flag to my friend over UDP, one character at a time, but it got corrupted! I think someone else was messing around with me and sent extra bytes, though it seems like they actually abided by RFC 3514 for once. Can you get the flag?
Initial findings
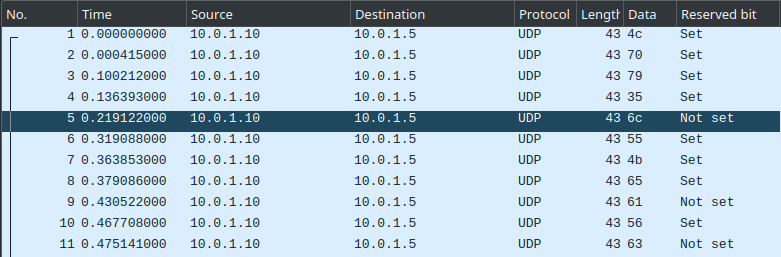
With the challenge, we get a Wireshark packet capture file named EBE.pcap
In this capture, there are 308 UDP frames, all containing one (1) single character as data. We know the flag format is lactf{FLAG_TEXT}, so we can discriminate between the first few flag and extra frames. It was at this point I noticed something curious: the reserved bit of all extra frames is set, while the frames containing the flag have it not set.
You could make a filter for that!

Making the filter
This was a learning experience for me too, as I have not worked with Wireshark before, after some quick googling, I found you can build filters of most kinds very easily. In this case, I selected the reserved bit from flags of the internet protocol, and filtered for not set.
ip.flags.rb != 1

Decoding the flag
After I had that, I just copied the data fields of each frame, which are hex numbers for ASCII characters, into a hex to ASCII converter. The end result is:
hex: 6C 61 63 74 66 7B 33 56 31 4C 5F 38 31 37 5F 33 78 66 31 6C 37 52 34 37 31 30 4E 5F 34 5F 37 48 33 5F 57 31 4E 5F 35 31 44 34 33 63 38 30 30 30 30 33 34 64 30 63 7D
which translates into:
lactf{3V1L_817_3xf1l7R4710N_4_7H3_W1N_51D43c8000034d0c}
If you enjoyed this CTF writeup, check out other writeups I wrote!